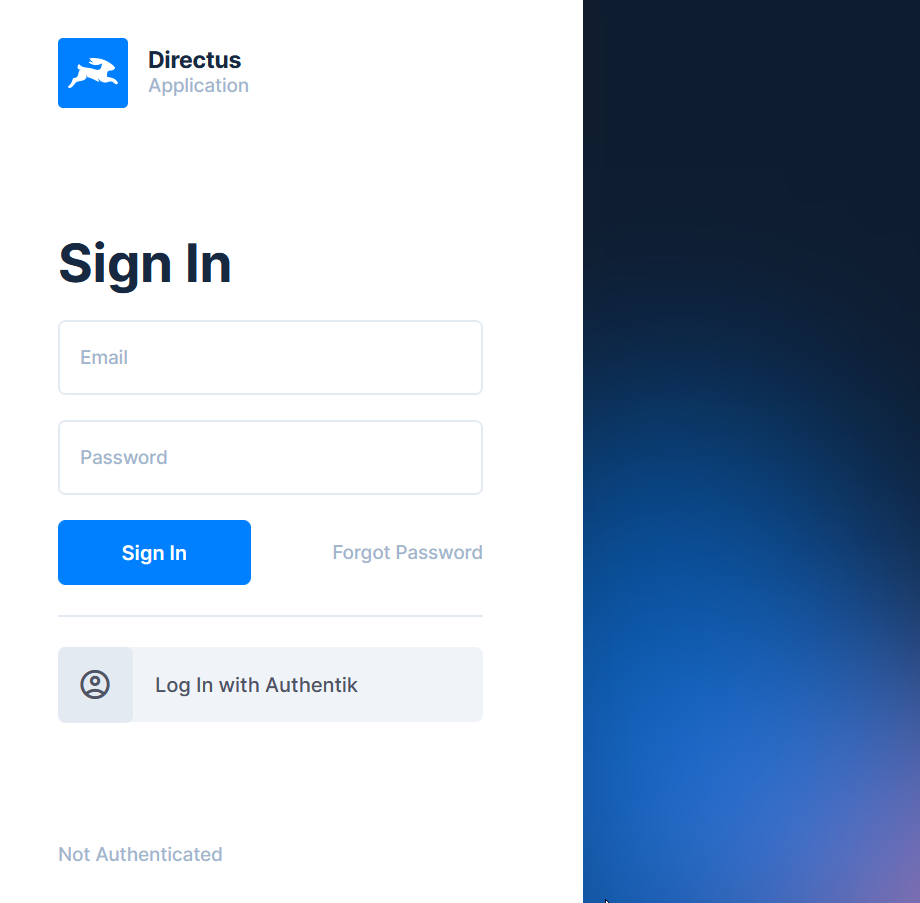
Look just like you, I was scoring the internet for Authentik -Directus integration example, only to find myself in the deep rabbit hole of StackOverflow, error codes and github issues page. It is actually not impossible and I will try to be as direct on this long path.
Installing Directus
Method 1: Docker
Create a new empty folder on your Desktop called directus. Within this new folder, create the three empty folders database, uploads, and extensions.
Copy and paste the following and save the file as docker-compose.yml:
version: "3"
services:
database:
image: postgis/postgis:13-master
# Required when running on platform other than amd64, like Apple M1/M2:
# platform: linux/amd64
volumes:
- ./data/database:/var/lib/postgresql/data
environment:
POSTGRES_USER: "directus"
POSTGRES_PASSWORD: "directus"
POSTGRES_DB: "directus"
cache:
image: redis:6
directus:
image: directus/directus:10.10.4
ports:
- 8055:8055
volumes:
- ./uploads:/directus/uploads
- ./extensions:/directus/extensions
depends_on:
- cache
- database
environment:
KEY: "255d861b-5ea1-5996-9aa3-922530ec40b1"
SECRET: "6116487b-cda1-52c2-b5b5-c8022c45e263"
DB_CLIENT: "pg"
DB_HOST: "database"
DB_PORT: "5432"
DB_DATABASE: "directus"
DB_USER: "directus"
DB_PASSWORD: "directus"
CACHE_ENABLED: "true"
CACHE_STORE: "redis"
REDIS: "redis://cache:6379"
ADMIN_EMAIL: "[email protected]"
ADMIN_PASSWORD: "d1r3ctu5"
# Make sure to set this in production
# (see https://docs.directus.io/self-hosted/config-options#general)
# PUBLIC_URL: "https://directus.example.com"
# Environment variables can also be defined in a file (for example `.env`):
# env_file:
# - .envdocker compose upMethod 2: Directus CLI & PM2
Install Node.js v18, specifically version 18.17 >= 19.11 (less than v20) use NVM to change versions, YARN and PM2 .
For server-side CLI, all functionality can be accessed by running npx directus <command> in your project folder.
Initialize a New Project
npm init directus-project <project-folder>or reconfigure existing project via npx directus init
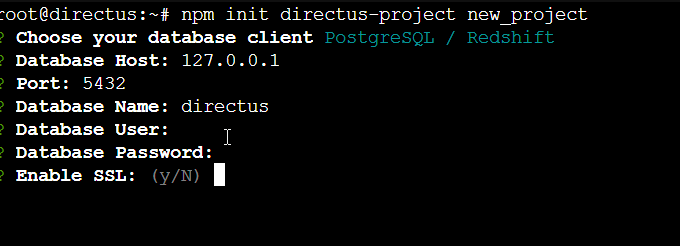
After configuring through the interface deploy in development mode by starting the Directus server over 0.0.0.0:8055.
npx directus start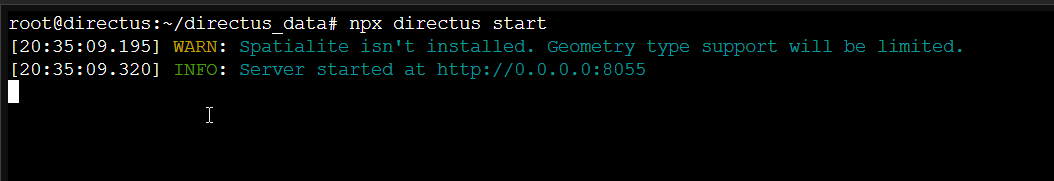
Deploying Directus in production via PM2
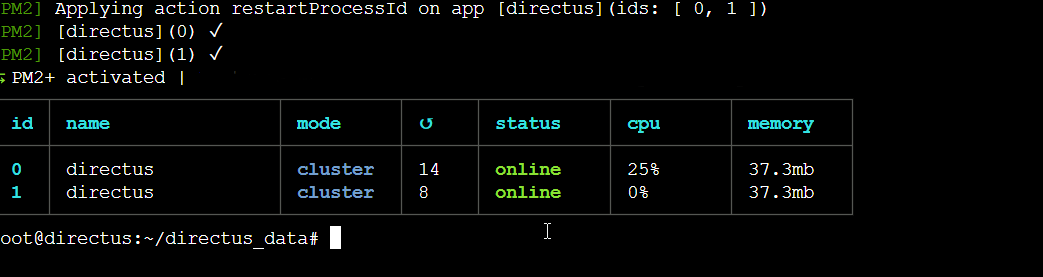
In production, you may need persistence,scaling and monitoring ability, which cli lack in features. Its recommended to use PM2 , a lighweight and popular application server over PhusionPassenger.
Install PM2 as shown, then Change directory into Directus project folder.
To initiate creation of ecosystem.config.js file use the ecosystem command and edit the files as shown:
pm2 ecosystemmodule.exports = {
apps : [{
name : "directus",
instances : "2",
exec_mode : "cluster",
script : "npx",
args : "directus start",
autorestart : false,
watch: false,
max_memory_restart: "2G"
}]
}
Installing Authentik
To download the latest docker-compose.yml open your terminal and navigate to the directory of your choice. Run the following command:
wget https://goauthentik.io/docker-compose.ymlIf this is a fresh authentik installation, you need to generate a password and a secret key. If you don't already have a password generator installed, you can run this command to install pwgen, a popular generator:
# You can also use openssl instead: `openssl rand -base64 36`
sudo apt-get install -y pwgenBy default, authentik listens internally on port 9000 for HTTP and 9443 for HTTPS. To change the exposed ports to 80 and 443, you can set the following variables in .env:
COMPOSE_PORT_HTTP=80
COMPOSE_PORT_HTTPS=443Afterwards, run these commands to finish or follow more on offical docs:
docker compose pull
docker compose up -dConfiguring Authentik OpenID
After configuring Authentik server, login into the Admin Settings and create new Application and Provider for Directus as OAuth2/OpenID Provider
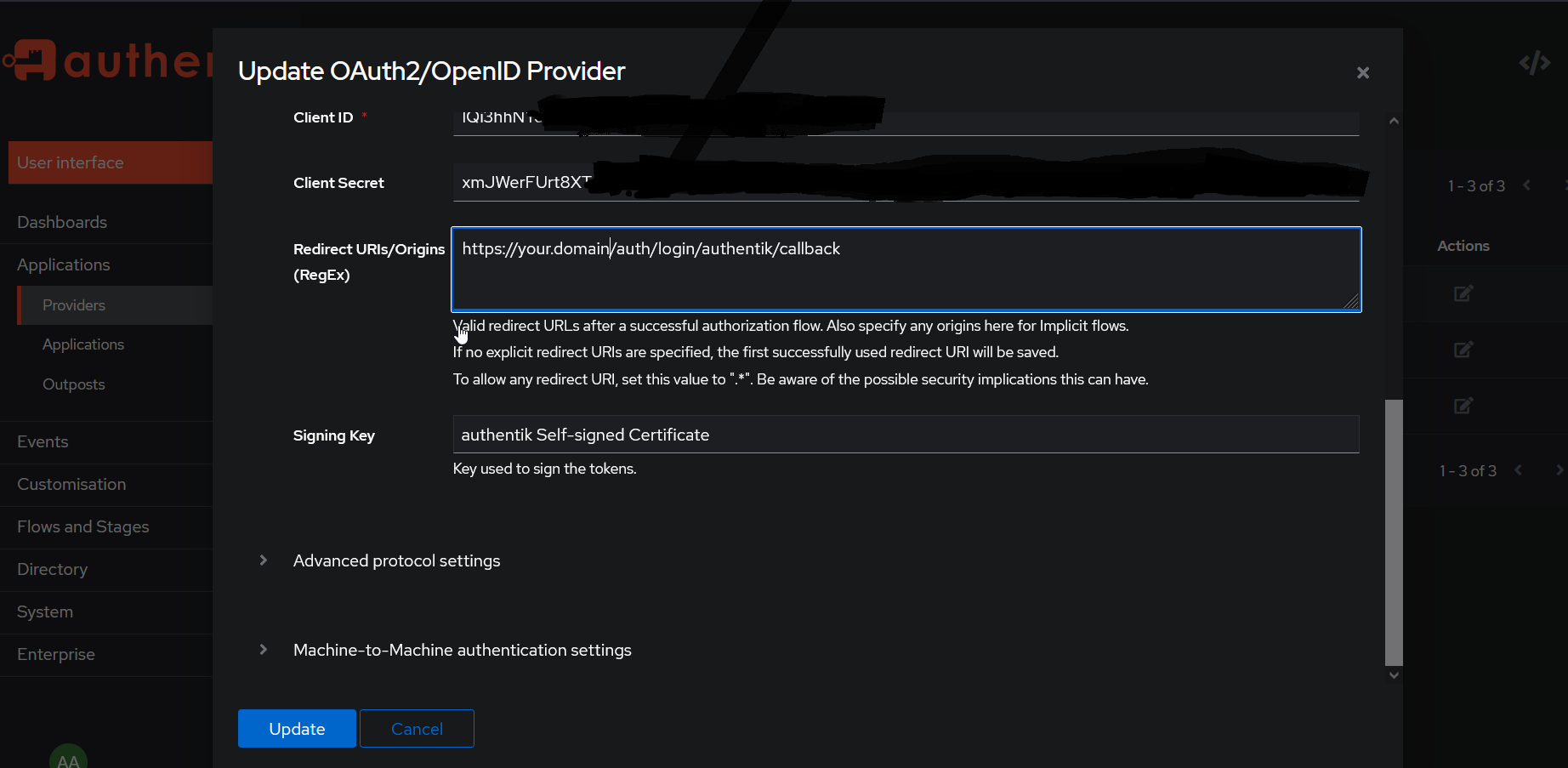
Configuring Directus SSO to Authentik
Copy Provider Client ID ,Client Secret and validate Redirect URI matches that of Directus domain.
Directus supports four standard types of SSO mechanisms:
These are well supported within Authentik. Using the default Directus Admin Login into the Dashboard -> Users ->Administrator. Note the URL https://your.domain/admin/users/1113322-aba6-1c9c-1234-123423681234
To add Single Sign On (SSO) to Directus, obtain a client ID and client secret from your authentication provider and add them to your env configuration file along with the required parameters below.
- AUTH_AUTHENTIK_DRIVER="openid"
- AUTH_AUTHENTIK_CLIENT_ID=(from Authentic Provider shown above)
- AUTH_AUTHENTIK_CLIENT_SECRET=
- AUTH_AUTHENTIK_ISSUER_URL= (location of /.well-known/openid-configuration ie https://your.domain/application/o/directus/.well-known/openid-configuration)
- AUTH_AUTHENTIK_IDENTIFIER_KEY=email
- AUTH_AUTHENTIK_ALLOW_PUBLIC_REGISTRATION (true or false)
- AUTH_AUTHENTIK_DEFAULT_ROLE_ID (Role ID from Directus ie;1113322-aba6-1c9c-1234-123423681234)
AUTH_PROVIDERS="authentik"
AUTH_AUTHENTIK_DRIVER="openid"
AUTH_AUTHENTIK_CLIENT_ID="client-id-authentik"
AUTH_AUTHENTIK_CLIENT_SECRET="client-secret-authentik"
AUTH_AUTHENTIK_ISSUER_URL="https://authentik.domain.com/application/o/directus/.well-known/openid-configuration"
AUTH_AUTHENTIK_IDENTIFIER_KEY="email"
AUTH_AUTHENTIK_ALLOW_PUBLIC_REGISTRATION="true"
AUTH_AUTHENTIK_DEFAULT_ROLE_ID="1113322-aba6-1c9c-1234-123423681234"Common issues
Authentik fails with error "The request fails due to a missing, invalid, or mismatching redirection URI (redirect_uri)." This means to check redirect URL in OpenID Provider within Authentik
Directus fails to login with INVALID_FOREIGN_KEY "https://your.domain/admin/login?reason=INVALID_FOREIGN_KEY". This means the used AUTH_AUTHENTIK_DEFAULT_ROLE_ID is invalid, check the admin URL to validate.
Directus fails to login with INVALID_PROVIDER"https://your.domain/admin/login?reason=INVALID_PROVIDER". Check that the .env has correct AUTH_PROVIDERS that is 'authentik' is included without # sign for line there.
Directus fails to login with INVALID_CREDENTIALS "https://your.domain/admin/login?reason=INVALID_CREDENTIALS". Check that the the Directus user/administators have unique email to your OpenID users. If the email exists SSO user will fail to authenticate (password preceedes SSO)
Conclusion
Successfully logged in to Directus with Authentik. New account appears within Administrators and heaven is happy. Holla to know this helped [email protected]